Which Internet Fraud Involves Using Social Engineering Techniques
This study examined the contents of 100 phishing e-mails and 100 advance-fee-scam e-mails and evaluated the persuasion techniques exploited by social engineers for their illegal gains. Which Internet fraud involves using social engineering techniques and attempts to deceptively gain private information by masquerading as a legitimate business organization.

Social Engineering Attacks Prevention And Best Practices Loginradius Loginradius Blog
Advantages And Disadvantages Of Cloud Storage.

. Cloud Computing Security Issues and Challenges. As one of the most popular social engineering attack types phishing scams are email and text message campaigns aimed at creating a sense of urgency curiosity or fear in victims. Cyber criminals behind this fraud are using social engineering techniques to encourage victims to perform secondary actions like initiating wire transfers.
Risk Assessment Hygiene Are Key. Difficult to Define Quick to Grow. Internet crime schemes steal millions of dollars each.
What is it called when criminals sift through trash for information. Social engineering is a cybersecurity threat that takes advantage of the weakest link in our security chain our human workforce to gain access to corporate networks. It then prods them into revealing sensitive information clicking on links to malicious websites or opening attachments that contain malware.
Common Social Engineering Techniques. Social engineering techniques Phishing is a criminal activity that involves using _______________________ and attempts to deceptively gain private information like usernames PIN numbers passwords and credit card details by masquerading as a legitimate business organization typically in a legitimate looking email. In the context of information security social engineering is the psychological manipulation of people into performing actions or divulging confidential information.
Use of phone or internet to phish for data that could be used for pretexting sending malware or to obtain information. In its 2021 Data Breach Investigations Report for instance Verizon Enterprise found that social engineering was the most common attack vector in data breaches observed in 2020 and the third most. Use of phone or internet to phish for data that could be used for pretexting sending malware or to obtain information.
It compromises legitimate email accounts through social engineering techniques to submit unauthorized payments. What keeps unauthorized Internet users out of private intranets. Social engineering techniques can take many forms.
SOCIAL ENGINEERING FRAUD TECHNIQUES Pretexting. What is the most uncomplicated Internet fraud. An attacker can familiarize himherself with the users of the target system prior to the social engineering attack.
A sophisticated form of attack targeting businesses that frequently make wire payments. To avoid hackers internet fraud attempts users need to understand common examples of internet fraud and tactics. Criminal actors using insider threat to conduct SIM swap schemes pay off a mobile carrier employee to switch a victims mobile number to a SIM card in the criminals possession.
Hacker impersonates someone in authority in an effort to obtain personal information or some sort of action. Which Internet fraud involves using social engineering techniques. Social engineering involves a criminal actor impersonating a victim and tricking the mobile carrier into switching the victims mobile number to a SIM card in the criminals possession.
Phishing What keeps unauthorized Internet users out of private intranets. SOCIAL ENGINEERING FRAUD TECHNIQUES. A type of confidence trick for the purpose of information gathering fraud or.
The following is the list of the commonly used techniques. This differs from social engineering within the social sciences which does not concern the divulging of confidential information. Which Internet fraud involves using social engineering techniques.
The Internet of Things. Attackers use increasingly sophisticated trickery and emotional manipulation to cause employees even senior staff to surrender sensitive information. Uses voice response system designed to.
Internet fraud is the use of Internet services or software with Internet access to defraud victims or to otherwise take advantage of them. Users are less suspicious of people they are familiar with. Hacker impersonates someone in authority in an effort to obtain personal information or some sort of action.
Business email compromise BEC. The 4 Crucial Aspects Of Cloud Security. IVR Phone Phishing.
Smishing It is a phishing attack method carried out by attackers over text messages or messaging apps to deceive the victim and tricking them into giving sensitive information credentials etc. Social engineering is a psychological exploitation which scammers use to skillfully manipulate human weaknesses and carry out emotional attacks on innocent people.
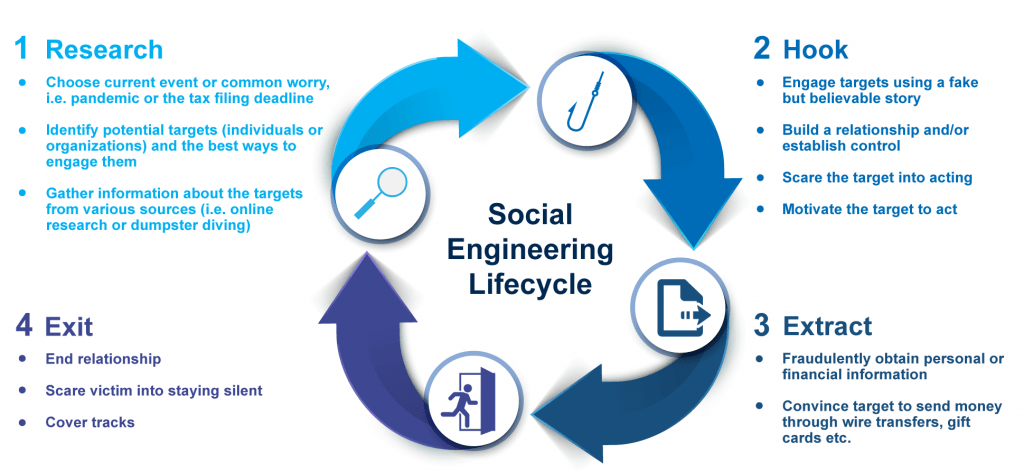
Social Engineering What It Is And How To Prevent It Bsg Blog
Social Engineering What It Is And How To Prevent It Bsg Blog

What Is Social Engineering Examples Prevention Tips Managed It Services And Cyber Security Services Company Teceze

What Is Social Engineering 4 Types Of Attacks Tessian

Social Engineering How Hackers Get At Your Date

15 Examples Of Real Social Engineering Attacks Updated 2022

Social Engineering Attacks Download Scientific Diagram

What Is Social Engineering Definition And Protection Tips For 2022 Upguard

What Is Social Engineering Fraud Epic Insurance Brokers Consultants

Social Engineer Gw Information Security Blog

Social Engineering Attacks A Look At Social Engineering Examples In Action Hashed Out By The Ssl Store

Pdf Defining Social Engineering In Cybersecurity

Social Engineering What It Is And How To Prevent It Bsg Blog

7 Social Engineering Scams That Could Affect Your Business

Pdf A Study Of Social Engineering In Online Frauds

5 Social Engineering Attacks To Watch Out For The State Of Security

Comments
Post a Comment